Too often, product security compliance is treated as a one-off exercise, a box to tick late in the go-to-market process. It shows up as a last-minute scramble: chasing documents, filling checklists, resubmitting evidence, and negotiating with labs under pressure. For many product teams, security compliance isn’t built into product development, it’s bolted on afterward, seen as a roadblock rather than an enabler.
But the reality has changed. Market needs and requirements have evolved as security compliance for radio connected devices is now mandatory in the EU and other countries, regions are following the EU’s lead. Directives and regulations such as the Radio Equipment Directive Delegated Act (RED-DA) and the Cyber Resilience Act (CRA) aren’t just legal requirements. They safeguard reputation, build trust with end consumers, and ultimately decide which companies can adapt, respond to market demands, and launch products with confidence.
The challenge is clear: while regulatory demands have grown dramatically, the industry’s methods for managing product security compliance haven’t kept up.
While some security compliance teams may have put proper governance processes in place, they far too often still lack the tooling and performance measurement that SDLC teams take for granted. Developers measure velocity, quality, implementation of security parameters and coverage. Security compliance teams? Too often stuck with manual checklists. And IT security-centric GRC platforms in the market don’t address the realities of connected devices.
Modern connected devices also rely on a web of suppliers. In software development, dependency scanning and automated tests make sure vulnerabilities in third-party components don’t slip through. But in security compliance, supplier checks are still manual and fragmented: procurement reviews contracts, product security assesses risks, security compliance maps against standards… It’s rarely in sync. Without a common system of record, one supplier misstep can stall certification or damage reputations.
That’s why we started working on a comprehensive Product Security Compliance Operations framework: one that doesn’t just focus on governance but also on performance and efficiency as its core building blocks.. We call it the PSCOPE Maturity framework, PSCOPE stands for “Product Security Operations Performance & Efficiency”. It’s still early-stage and evolving, but we believe it holds promise to reshape how product security compliance is managed. Our goal is to prove it works in practice, together with the community.
Product Security Compliance Challenges: Going back to 2020
Let’s rewind to 2020. At the time, I was leading the digital transformation of the device security activitiesat UL Solutions’ Identity Management & Security division. Mymission was straightforward: make product security compliance more efficient,transparent and collaborative.
What we found from our customers as well as our own processes needed considerable improvements. Each new product security evaluation felt like starting from scratch:
- Scattered documentation – Evidence buried in PDFs, spreadsheets, and emails.
- Supplier silos – Critical compliance data missing or delivered inconsistently.
- Manual processes – Teams spending weeks (even months!)collecting, formatting, and submitting evidence by hand.
- Disconnected ownership – Security teams building controls, security compliance teams handling labs, with little collaboration.
- Long review cycles – Labs requesting clarifications, resubmissions, and fresh documentation.
Meanwhile, regulations were expanding. ETSI EN 303 645 set out cybersecurity requirements for consumer IoT. RED-DA around 2022 extended rules to radioequipment. And the CRA now raises the bar for cybersecurity obligations across all connected products sold in the EU.
What could have been a differentiator had companies prepared to automate their processes for better performance and efficiency has become an even bigger burden. Teams are scrambling to deliver proofs and evidence of conformity, once again treating product compliance as a one-off exercise.
Manufacturers are expected not only to meet requirements, but to prove it continuously, across multiple geographies, with airtight documentation. Yet many organizations still rely on workflows designed for a different era.
The truth? Security compliance isn’t broken because regulations are unreasonable. It’s broken because the processes for managing security compliance haven’t evolved.
That’s where PSCOPE comes in.
What Is PSCOPE? A Product Security Compliance Operations Framework
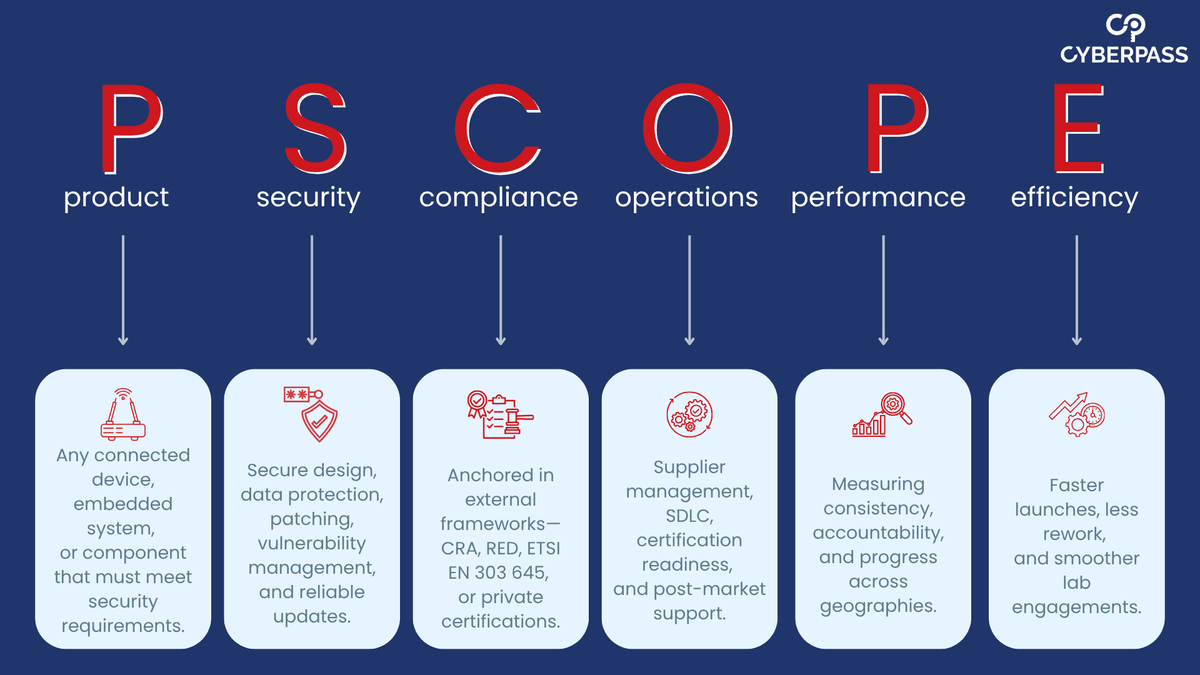
PSCOPE stands for Product Security Compliance Operations Performance & Efficiency.
It’s not just another checklist. PSCOPE is an emerging maturity framework designed to evaluate how effectively organizations manage and scale product security compliance. It’s built on industry experience, but it’s also deliberately open-ended: it will continue to evolve as we test it in real-world contexts and gather feedback from manufacturers.
Here’s how each letter breaks down:
- P = Product: Any connected device, embedded system, or component that must meet security requirements. From smart thermostats to industrial controllers, if it’s regulated—it’s in scope.
- S = Security: Cybersecurity-specific compliance: secure design, data protection, patching, vulnerability management, and update mechanisms.
- C = Compliance: Anchored in external frameworks: CRA, RED, ETSI EN 303 645, or private certification schemes.
- O = Operations: Compliance as lived reality: embedded in governance, supplier management, SDLC, certification readiness, and post-market support.
- P = Performance: Focused on execution: measuring consistency, accountability, and progress across products and geographies.
- E = Efficiency: The ultimate goal: faster launches, reduced rework, and smoother lab engagements.
All together, PSCOPE provides a shared language and measurement system for manufacturers, suppliers, labs, and regulators.
More importantly, it reframes security compliance as an operational capability:not a project to finish, but a discipline to master for sustainable execution
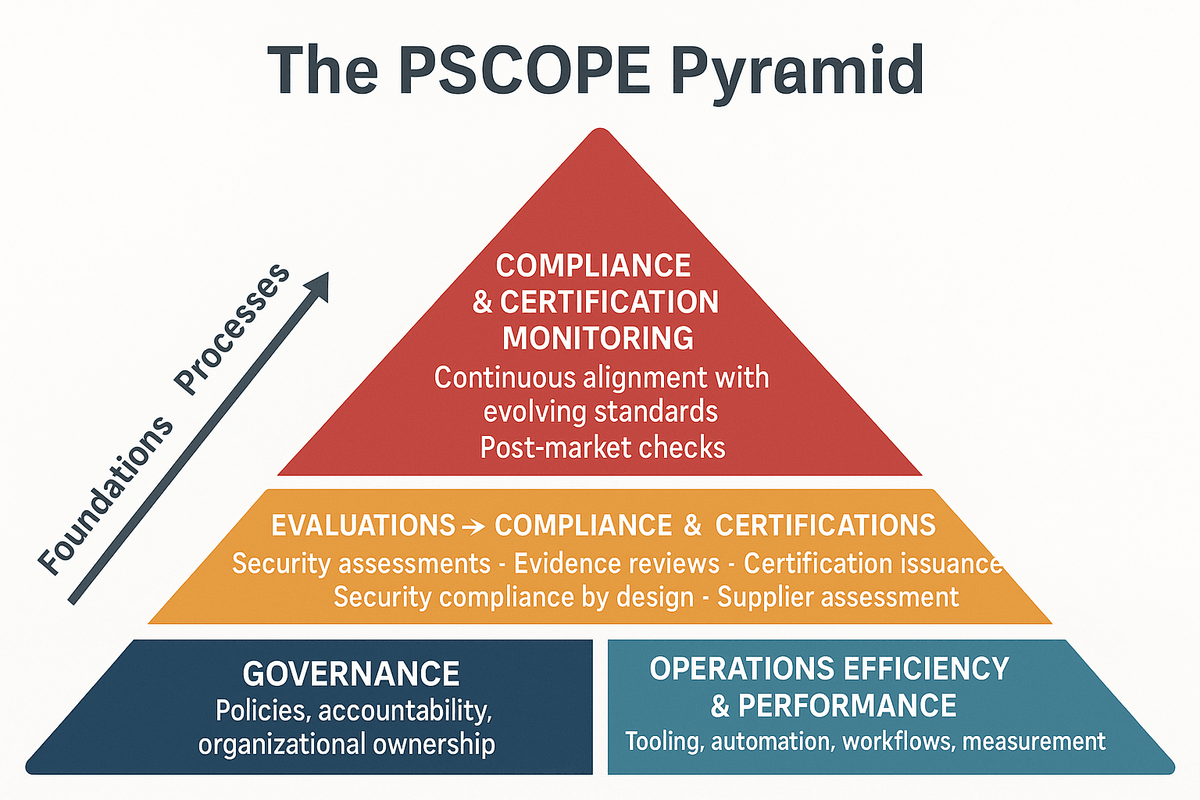
PSCOPE Maturity Model: Step-by-Step Product Security Compliance Levels
To move security compliance from reactive to strategic, PSCOPE uses a five-level maturity model (inspired by CMMI). Each pillar reflects a critical dimension of product security compliance.
1. Governance and Readiness
- Level 1 – Initial: Governance absent or ad hoc - No formal policies, undefined roles, reactive decision making
- Level 2 – Managed: Basic policies & roles - Policies drafted, roles assigned, some oversight, but inconsistent enforcement
- Level 3 – Defined: Governance institutionalized - Governance structured, roles & responsibilities formal, decision paths defined
- Level 4 – Quantitatively Managed: Metrics & oversight - KPIs and dashboards, audit/tracking, formal governance reviews
- Level 5 – Optimizing: Adaptive governance - Governance evolves with regulatory change, continuous feedback & improvement
2. Automation Level
- Level 1 – Initial: Evidence managed in spreadsheets and PDFs.
- Level 2 – Managed: Repeatable manual processes.
- Level 3 – Defined: Automated tools for checklists and traceability.
- Level 4 – Quantitatively Managed: Data-driven decisions, performance analytics.
- Level 5 – Optimizing: Fully instrumented with real-time alerts and integrations.
3. Supply Chain Integration
- Level 1 – Initial: Suppliers uninvolved in compliance.
- Level 2 – Managed: Key suppliers provide occasional compliance data.
- Level 3 – Defined: Standardized supplier documentation and workflows.
- Level 4 – Quantitatively Managed: Supplier compliance tracked with deviations flagged.
- Level 5 – Optimizing: Dynamic dashboards and collaborative compliance workflows.
4. Self-Declaration / Certification Efficiency
- Level 1 – Initial: Manual, irregular lab submissions.
- Level 2 – Managed: Some evidence reuse, but inconsistent.
- Level 3 – Defined: Predictable lab cycles based on workflows.
- Level 4 – Quantitatively Managed: SLA-driven lab cycles, feedback loops analyzed.
- Level 5 – Optimizing: Push-button readiness, continuously reduced certification cycles.
5. Continuous Compliance Monitoring
- Level 1 – Initial: No post-market compliance processes.
- Level 2 – Managed: Patch plans and incident responses documented.
- Level 3 – Defined: Roles assigned, periodic validation.
- Level 4 – Quantitatively Managed: Metrics like patch timelines monitored.
- Level 5 – Optimizing: Automated monitoring, proactive detection, and remediation.
This maturity model is our first iteration. It offers a starting point for organizations to gauge where they are and what steps they might take to improve. Over time, with feedback and pilot applications, we will refine it further so it reflects the realities faced across different actors in the ecosystem.
How to Apply PSCOPE for Product Security Compliance Success
The beauty of PSCOPE is its practicality. You don’t need a massive transformation project to benefit. Instead, you climb one level at a time.
Here’s how organizations can start:
- Assess – Benchmark your current maturity across each pillar.
- Document – Collect evidence: workflows, policies, supplier data, dashboards.
- Plan – Identify the next-level improvements for each pillar.
- Validate – Use annual self-assessments or third-party reviews to track progress.
This approach turns product security compliance into a continuous improvement discipline, not a fire drill before regulationdeadlines.
Benefits of PSCOPE: Streamline Product Security Compliance & Gain Competitive Advantage
Three reasons:
The benefits of PSCOPE go beyond theory but they still need to be validated in practice. Here are the 3 reasons why we believe it can make a difference, and why we’re inviting organizations to help us put it to the test:
- Consistent – PSCOPE introduces a shared language for product security compliance operations. It draws inspiration from established maturity models but is tailored to the realities of connected products and evolving cyber regulations.
- Actionable – No guesswork, no fluff. PSCOPE lays out a practical roadmap that shows how to progress step by step. It helps you see where you stand today, and what to prioritize next to strengthen compliance operations.
- Scalable – PSCOPE starts by addressing manufacturers, who face the most immediate regulatory and market pressures. Adapted versions for labs and scheme owners may follow.
Instead of static checklists that box you in, PSCOPE is about maturity: helping organizations build resilience that grows with them and keeps pace with shifting regulations. In short: it’s not just about security compliance for your products, it’s about staying ready, relevant, and ahead.
Turning CRA & RED Compliance from Burden to Competitive Advantage
Here’s the truth: regulations like the CRA, RED, and ETSI EN 303 645 aren’t going away. If anything, they’ll expand. But that’s not bad news.
Organizations that embrace PSCOPE and the automation of product security compliance operations don’t just meet requirements. They:
- Launch faster by reusing evidence and minimizing lab delays.
- Build trust with regulators, customers, and partners.
- Stay ahead of regulatory changes instead of scrambling to catch up.
Security compliance done right reduces time-to-market, builds credibility, and turns regulatory pressure into business advantage.
With PSCOPE, we’re laying the foundation for product security compliance to become the strategic trust capability it was always meant to be. But it won’t happen in isolation. We are actively looking for organizations willing to test and refine this framework with us to prove its value, challenge its assumptions, and shape its future. The question isn’t just whether you have to comply but whether you’ll help shape how security compliance evolves, from hurdle to enabler of trust and innovation.
